Cybercriminals are taking advantage of a zero-day vulnerability in WinRAR, an old and trusted tool for storing files on Windows computers. They're using this flaw to go after traders and snatch away their money. This tricky situation was uncovered by Group-IB, a company that specializes in keeping the online world safe.
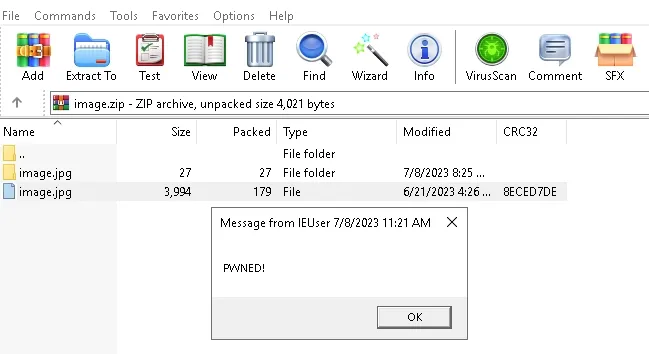
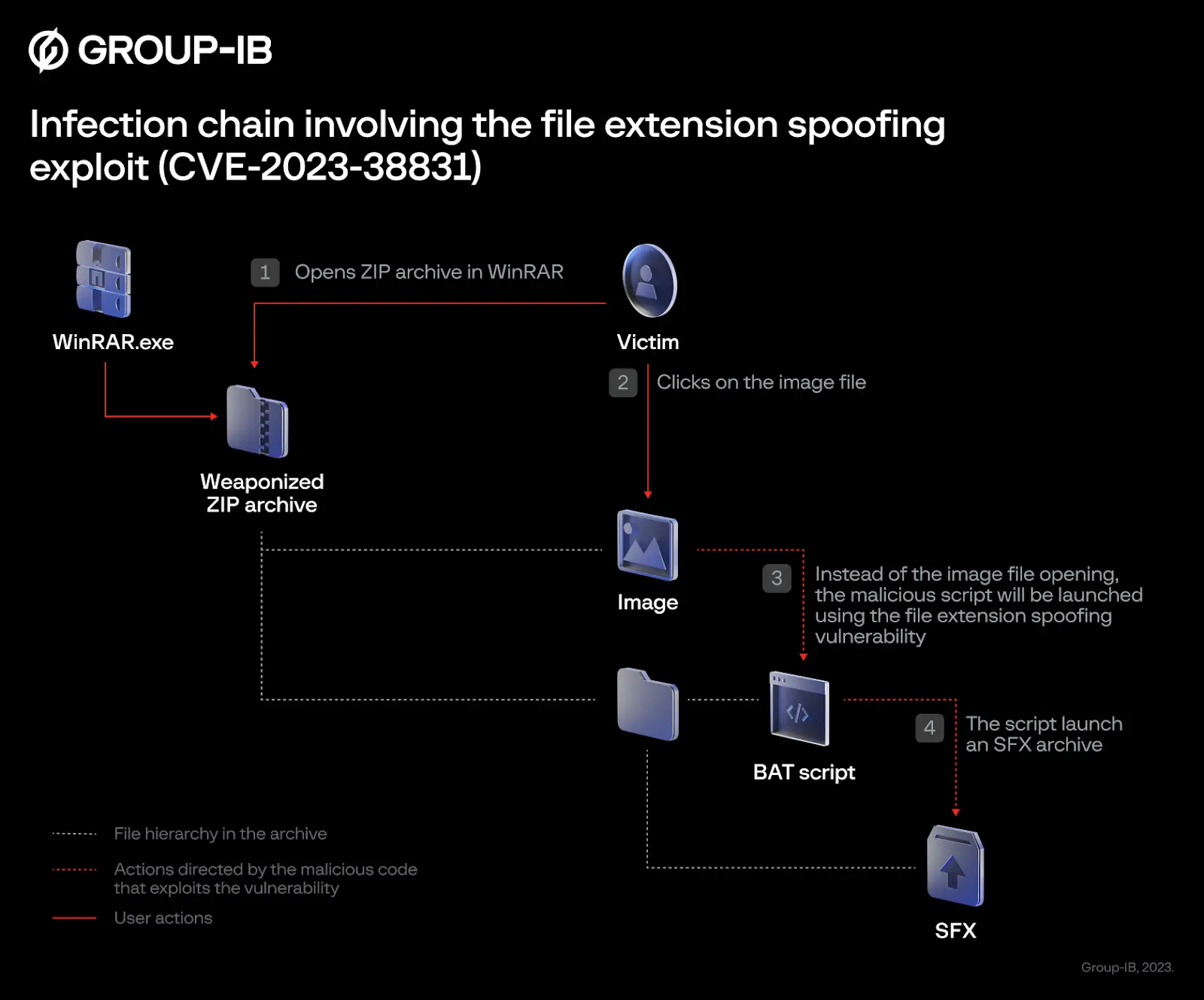
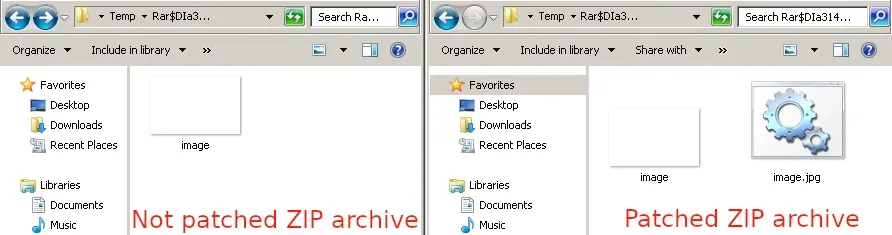
They found this weakness in June. Basically, this flaw messes with how WinRAR handles files in the ZIP format. Imagine this: They've managed to hide malicious scripts within archive files that appear innocent at first glance.
These scripts can pretend to be harmless ".jpg" images or ".txt" files. Once a user opens one of these seemingly benign files, the hackers gain access to their victim's device. This tactic is like a Trojan horse, where the attackers sneak in through the disguise and compromise the targeted machines.
Who are the hackers going after? It seems they've set their sights on a specific group: traders. These individuals who are involved in trading and investments have become prime targets. Cybercriminals have been spreading malicious ZIP archives across specialized trading forums.
The cybercriminals' strategy continues beyond the type of forums they're targeting. These malicious ZIP archives have been posted on public forums dedicated to various trading topics.
From trading strategies to investment tips and cryptocurrency discussions, these forums have unknowingly become platforms for cybercriminals to spread their harmful files.
The forum administrators, once they caught wind of these malicious files, did their best to thwart the attack. They issued warnings to their users and even blocked the accounts being used by the hackers. However, the hackers were not easily deterred.
They managed to unlock disabled accounts and continued their assault, spreading their malicious files through forum threads and private messages.
For those unfortunate users who open these tainted files, the consequences are dire. Once the malicious script takes hold, the hackers gain unauthorized access to the victims' brokerage accounts.
This gives them the power to engage in illegal financial activities, which include performing illicit transactions and withdrawing funds from these compromised accounts.
The impact of this attack is substantial. As of now, more than 130 traders' devices have been infected. The responsible hackers have been utilizing a VisualBasic trojan called DarkMe, which is linked to a group known as Evilnum. This group has a history of targeting financial organizations and online trading platforms.
Upon discovering this alarming situation, Group IB took action. They reported the vulnerability, known as CVE-2023-38831, to the makers of WinRAR, Rarlab. In response, Rarlab released an updated version of WinRAR (version 6.23) on August 2 to address the issue. This new version aims to patch the vulnerability and prevent further exploitation.
But that's not all. A separate vulnerability, known as CVE-2023-40477, has been fixed in WinRAR as well. This flaw allowed remote attackers to execute arbitrary commands on a targeted system.
The vulnerability was identified by a researcher named "goodbyeselene" of the Zero Day Initiative, who promptly reported it to Rarlab on June 8, 2023.
This vulnerability stemmed from an issue in the processing of recovery volumes. The flaw was a result of improper validation of user-supplied data, leading to a breach in memory access boundaries.
On the Common Vulnerability Scoring System (CVSS), this flaw received a severity rating of 7.8. While this might not seem extremely high, it's important to understand that attackers only need to trick a user into opening a compromised archive.
If you're using WinRAR, update to the latest version (6.23) released on August 2. This update addresses not only the CVE-2023-40477 vulnerability but also other issues that could potentially compromise your security. If you are not a premium user, you have to go manually to the website, download the exe, and install the latest version.
Whether you're using WinRAR or any other archiving tool, exercise caution when opening RAR files. Always be suspicious of unexpected files, especially if they're from unverified sources. Equally important is using a reliable antivirus tool that can scan archives for potential threats.
Sources: zerodayinitiative.com / group-ib.com












