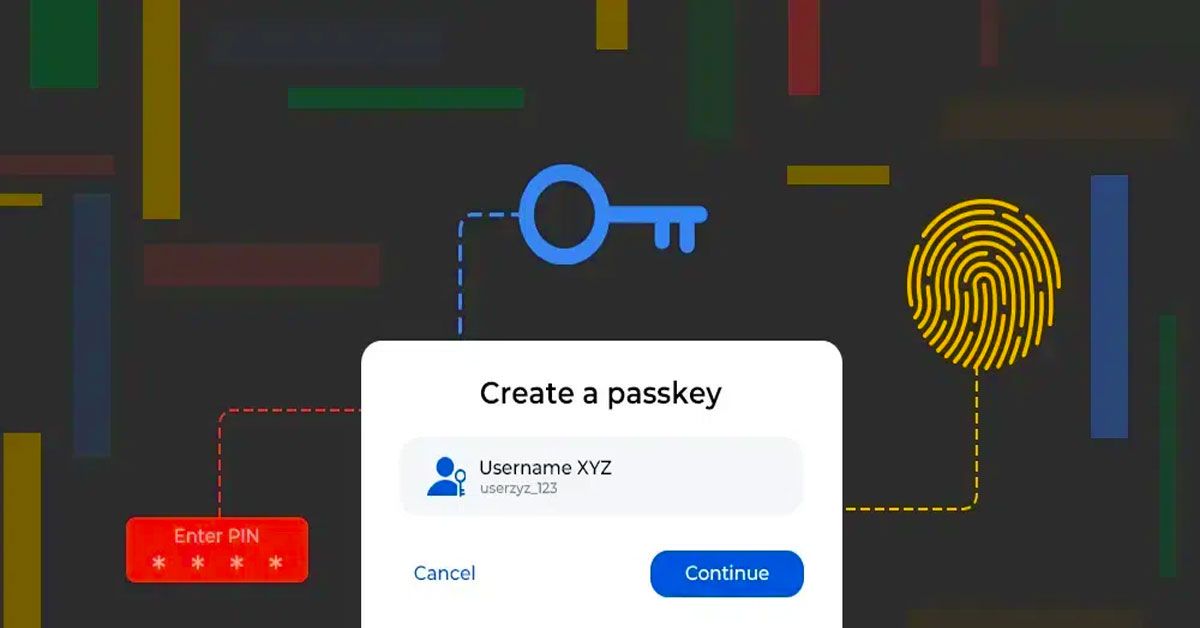
Are you tired of constantly having to remember and update multiple passwords for different accounts? Do you worry about the security of your online accounts and the potential for phishing attacks? Look no further than passkeys, the future of online authentication. Passkeys are:
- Digital credentials tied to a user account and a website or application.
- Enabling users to authenticate without entering a username or password.
- Additional authentication factor.
With passkeys, users no longer have to create and remember complex passwords and can enjoy a passwordless experience across different browsers and operating systems. Passkeys are standardized, built on FIDO standards, and provide robust protection against phishing attacks.
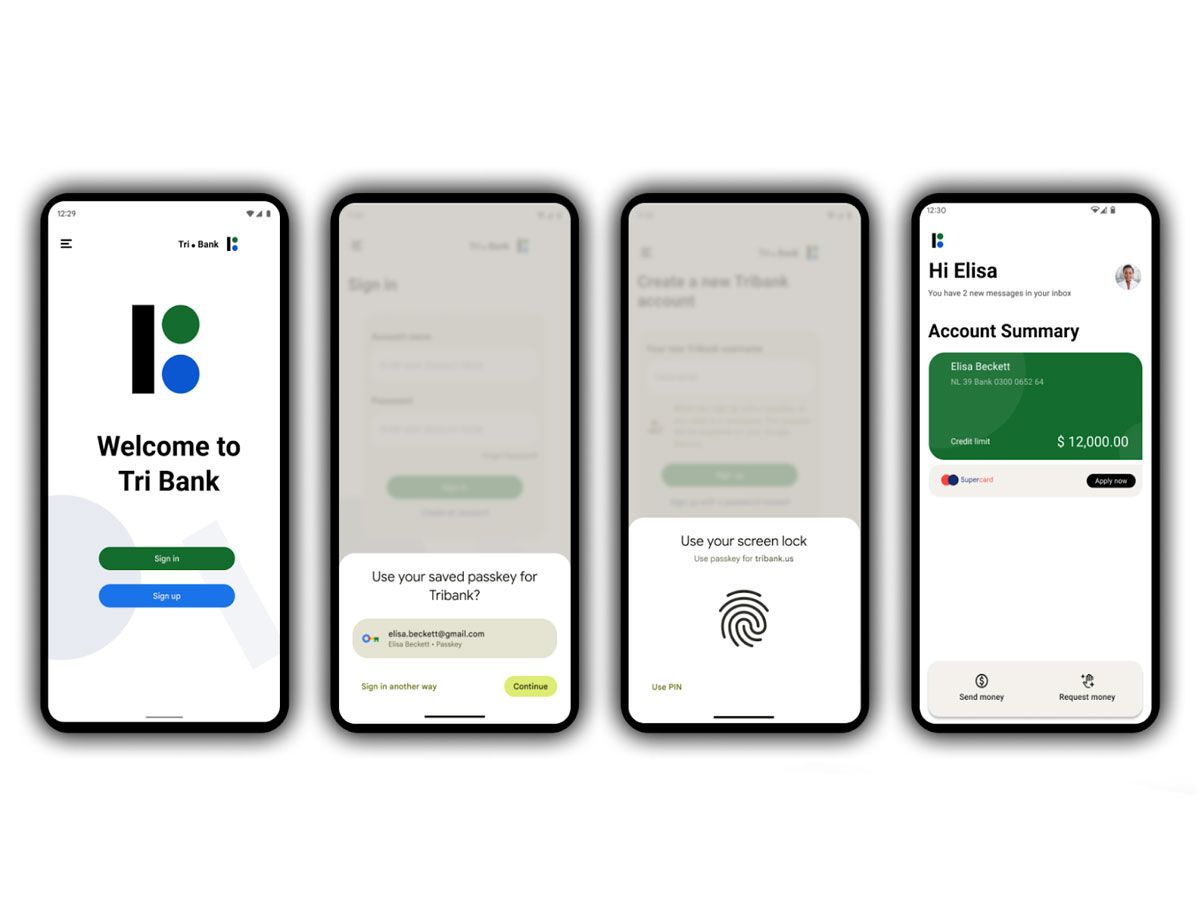
What are Passkeys?
Passkeys are digital credentials tied to a user account and a website or application that allows users to authenticate without entering a username, password, or additional authentication factor. Unlike passwords, users won't have to come up with a passkey to access an account. If passkeys are enabled on their Google account, they can have a unique one created for any site that they log into. Instead of entering a password, they would verify their identity on a trusted device with a PIN, fingerprint, or face scan.
Passkeys are not meant to be remembered by users but used by an online service to communicate directly with the device to help log in. Passkeys are built on FIDO standards, which means all browsers can adopt them. Passkey managers, such as Google Password Manager, protect passkeys from unauthorized access and use by encrypting passkey secrets end-to-end. Public key cryptography is used by passkeys, which reduces the risk of potential data breaches.
Passkeys are bound to a website or application's identity, making them safe from phishing attacks. The same passkey is never used with more than one site, and passkey protocols are designed to prevent information shared with sites from being used as a tracking vector. As a result, Google alleges your accounts would become much harder to hack.

How to Use Passkeys
To create a passkey for a website or application, a user must first register with that site or application and follow a few simple steps. Once the passkey is created, users can sign in to services on any device using a passkey, regardless of where the passkey is stored, as long as the device generating the signature is authorized.
Benefits of Passkeys
Passkeys are a safer and easier alternative to passwords, eliminating the need to create and remember complex passwords. They provide robust protection against phishing attacks and reduce the risk of potential data breaches. Passkeys are created to be compatible with various operating systems, such as iPhone, Android, Mac, and Windows computers. This makes them standardized and user-friendly.
FIDO, which stands for Fast IDentity Online, is an organization that sets standards for strong authentication protocols, such as passkeys. The FIDO Alliance has developed a set of standards for authentication that enable users to authenticate without entering a username, password, or additional authentication factor. This means that FIDO standards provide the framework for the creation and use of passkeys.
Passkeys and Phishing Attacks
One of the significant advantages of using passkeys is that they are standardized, meaning they work across different browsers and operating systems. This is possible because passkeys are built on FIDO standards, allowing all browsers to adopt them. By using FIDO standards, passkeys are designed to eliminate the need for different types of authentication factors across different sites and services. This means that passkeys provide a passwordless experience, making it easier and more secure to access online accounts.
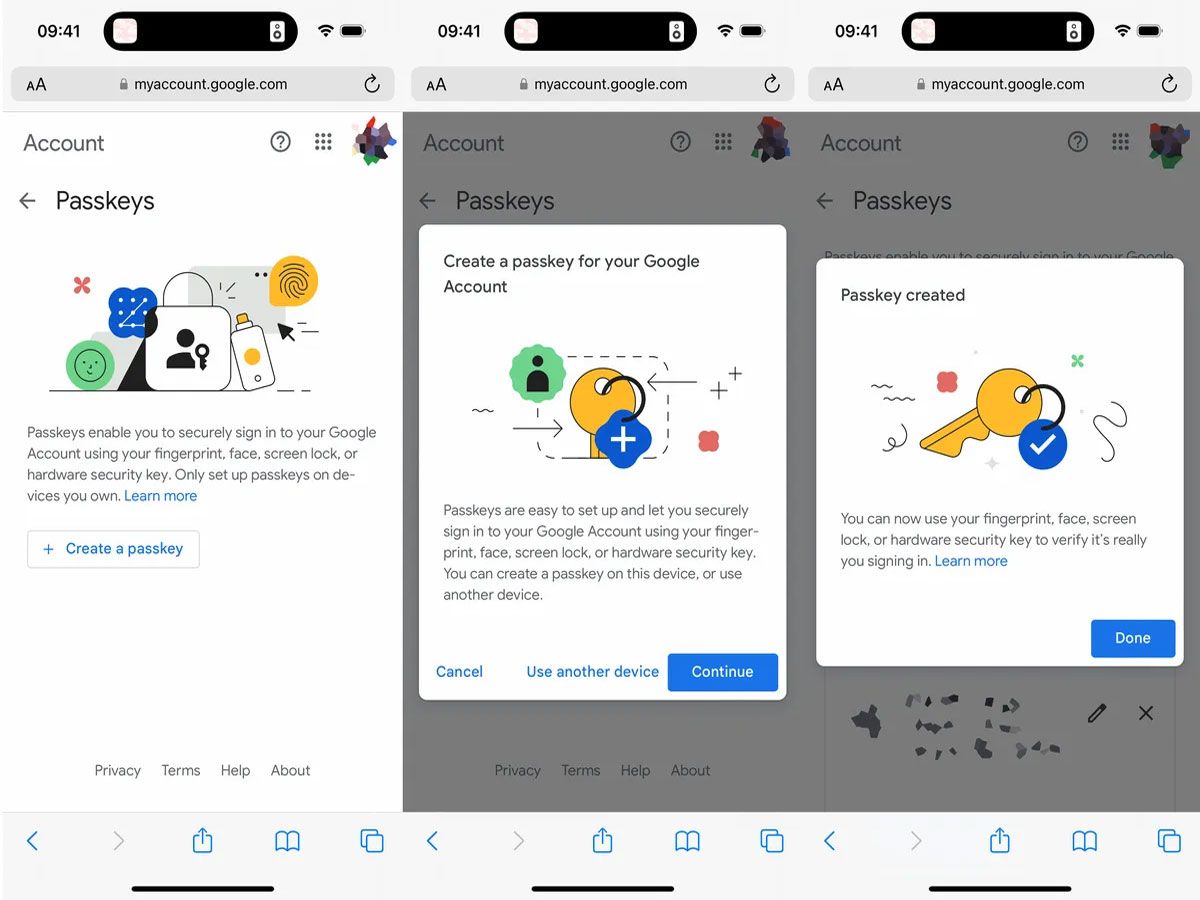
Phishing attacks are one of the most significant cybersecurity threats to online accounts. Phishing attacks trick users into divulging their usernames, passwords, or other sensitive information by posing as a trusted entity, such as a website or a company. However, passkeys provide robust protection against phishing attacks. Passkeys are bound to a website or application's identity, which makes them safe from phishing attacks. This means that even if a user enters their passkey on a fake website, the passkey cannot be used to authenticate to a different website or application.
Passkeys offer a safer, easier, and more secure alternative to traditional passwords. By leveraging the power of public key cryptography and FIDO standards, passkeys provide robust protection against phishing attacks while working seamlessly across different operating systems and devices. With the rise of online threats and data breaches, passkeys represent a significant step forward in digital security and privacy. As more companies and individuals embrace this technology, we can look forward to a future where accessing our online accounts is no longer a cumbersome and risky endeavor. So why wait? Start using passkeys today and experience the benefits for yourself. Your security and peace of mind are worth it.
Source: fidoalliance.org / developers.google.com / cnet.com / blog.google / android-developers.googleblog.com / cnn.com / wired.com / androidpolice.com