In a recent announcement on May 3, Google Registry introduced eight new top-level domains (TLDs) to the online world. These TLDs included .dad, .phd, .prof, .esq, .foo, .zip, .mov, and .nexus. While this news excited some, the introduction of the .zip and .mov domains triggered concerns among cybersecurity researchers and IT administrators. Why? Because these new domains resemble popular file extensions that cybercriminals often exploit for their malicious activities.
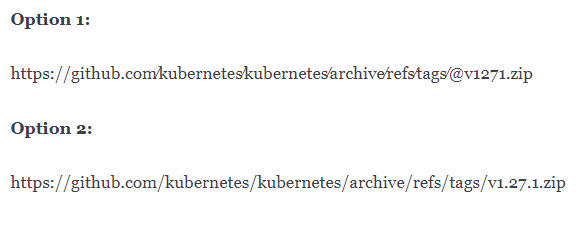
Imagine you stumble upon two URLs, and you need to determine which one is legitimate and which one is a cunning phishing attempt designed to unleash evil.exe.
Can you swiftly distinguish between these two URLs?
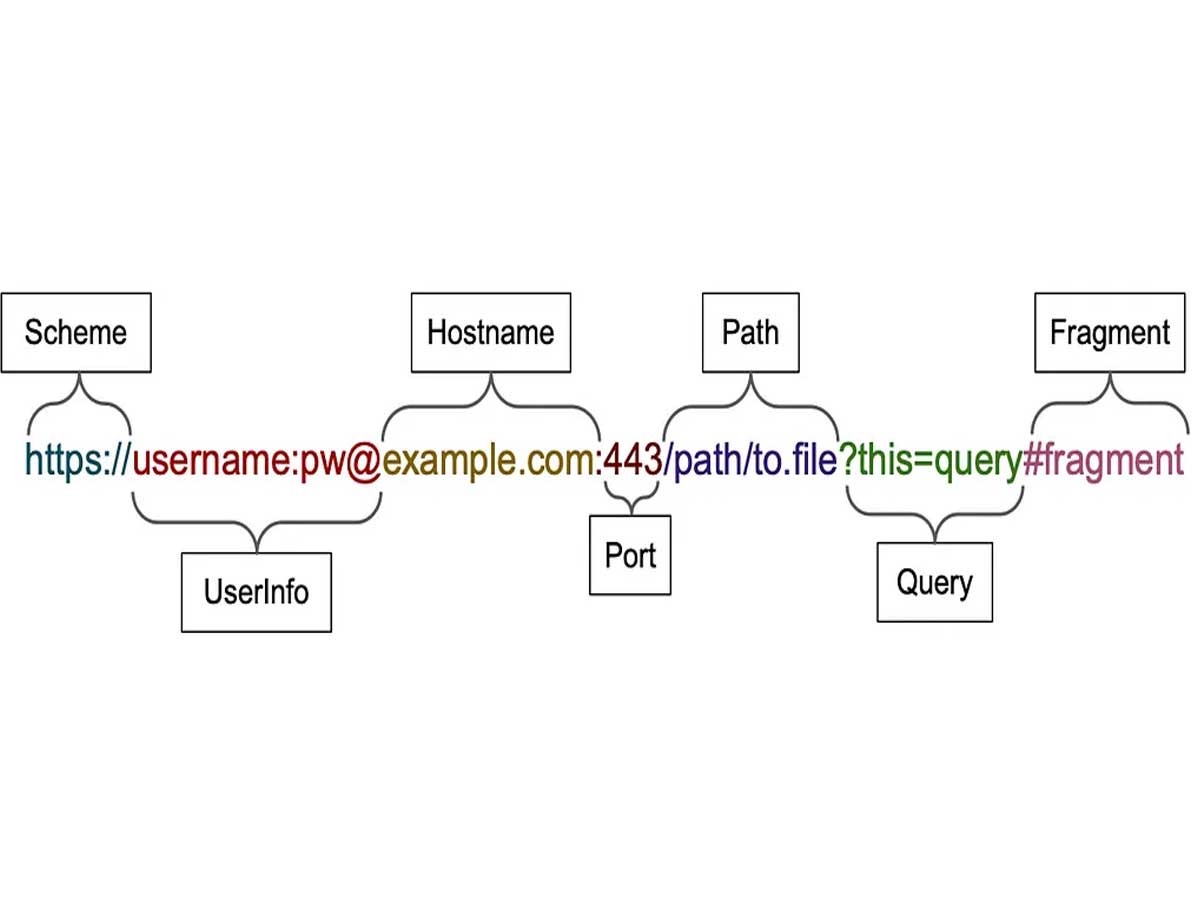
To understand the implications of Google's new TLDs, it's essential to grasp the difference between TLDs and file extensions. TLDs are the letters that appear after the dot in a domain name, while file extensions are the three letters that come after the dot in a file name. While these two elements serve different purposes, they both play significant roles in cyberattacks and online security.
The .zip file extension has long been associated with compressed files on Windows computers. Unfortunately, cybercriminals have recognized the potential of .zip files as malicious email attachments in their attack chains. These attackers often employ misdirection as a crucial element in their tactics, confusing both users and security software. They may even combine two file extensions to create deceptive filenames that mislead unsuspecting victims.
One of the primary concerns stemming from Google's introduction of .zip TLDs is the added layer of misdirection it enables. Attackers can now create malicious URLs that appear legitimate to users. These URLs could potentially trick individuals into thinking they are downloading harmless files when, in reality, they are unknowingly downloading viruses or other malware onto their devices. Scammers could even go a step further by crafting phishing sites that prompt users to enter their passwords for various websites, resulting in compromised accounts and sensitive information falling into the wrong hands.
The major challenge lies in the ability to create URLs that appear to originate from any domain. By using a combination of open redirects, recognizable words, and deceptive techniques, criminals can make their malicious URLs seemingly legitimate. For instance, they can employ the trick of including a username and password in the URL itself using the user info delimiter (@) and Unicode characters resembling slashes. This technique allows them to make a .zip file appear as if it is hosted on any website or path.
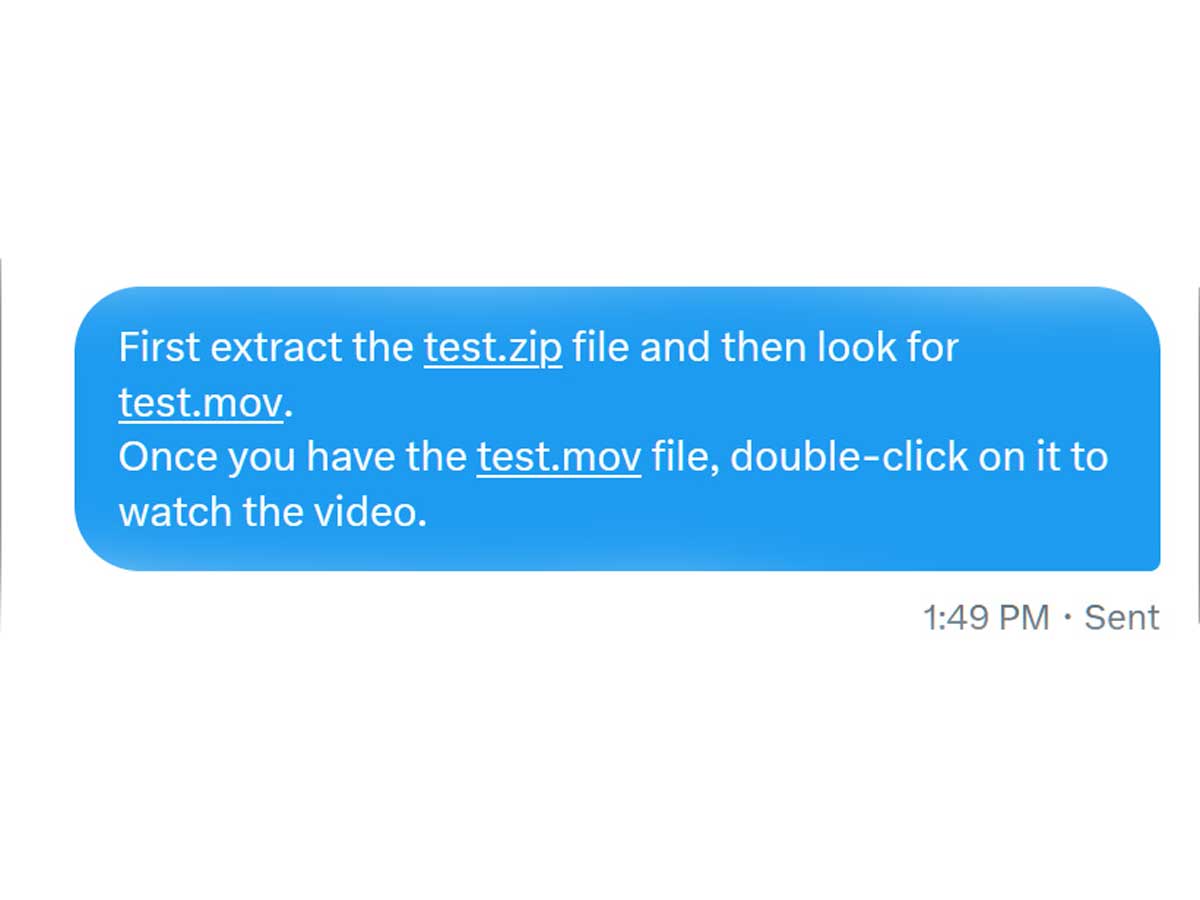
What makes the situation more concerning is that these malicious URLs can appear 100% legitimate, unlike traditional lookalike domains. Users who would otherwise exercise caution when encountering unfamiliar domains might fall victim to these deceptive tactics. When a link appears to come from a trusted company's primary domain, users are more likely to trust it and follow through, unknowingly exposing themselves to potential threats.
Detecting anomalies in URLs becomes increasingly challenging, even for those aware of potential threats. While there are limited combinations of lookalike characters that can be used in traditional domains, the introduction of .zip domains changes the game. With .zip TLDs, cybercriminals have the ability to create unlimited 100% lookalike domains for any website. This newfound freedom further complicates the task of identifying malicious URLs and protecting users from falling prey to phishing attacks.

Given the potential risks associated with Google's .zip and .mov TLDs, it is crucial to take appropriate measures to protect oneself from these threats. Several suggestions have been put forth by experts to mitigate the risks:
- Check for the presence of the user info delimiter (@) in URLs, as this is a red flag indicating a potential deception.
- Utilize third-party DNS services that offer the ability to block .zip domains, providing an additional layer of protection.
- Leverage security features and solutions provided by browsers, such as Google Safe Browsing, which help prevent confusion between domain names and file names.
- Please exercise caution when encountering .zip or .mov links, especially when they prompt users to download files or enter sensitive information. It is advisable to research the URLs and avoid clicking if unsure about their safety.
- Adhere to standard security practices, including not trusting unfamiliar links and files and being mindful of the potential risks associated with phishing sites.
Google's decision to introduce .zip and .mov TLDs has sparked a heated debate among developers, security researchers, and IT administrators. While some argue that the concerns are unwarranted, others firmly believe that these TLDs only add unnecessary risks to an already vulnerable online environment. As a result, individuals have begun registering .zip domains associated with common ZIP archives to raise awareness about the risks, share harmless information, or play pranks.
We are now the proud owner of your favorite initial access method pic.twitter.com/PGKqb7LqzC
— vx-underground (@vxunderground) May 12, 2023
In light of these emerging threats, it is crucial for industry players and individuals alike to address the issue and take necessary precautions actively. Some developers have already requested the removal of .zip TLDs from Mozilla's Public Suffix List, emphasizing the importance of maintaining valid TLDs while considering the potential risks they may pose. Collaboration between stakeholders, including domain registrars, security experts, and internet users, is key to mitigating the risks associated with these new TLDs.
As we navigate the evolving landscape of cybersecurity, the introduction of .zip and .mov top-level domains (TLDs) by Google brings excitement and concern. It's a reminder that we must remain vigilant in protecting ourselves online. However, I believe that by staying informed, adopting best practices, and fostering a culture of cybersecurity awareness, we can confidently embrace the digital world while minimizing the risks. Let's empower ourselves and collaborate with developers, security researchers, and IT administrators to create a safer online environment. Together, we can shape a future where we can explore the vast possibilities of the internet with peace of mind.
Sources: github.com / malwarebytes.com / bleepingcomputer.com / support.google.com / domains.google / chromium.googlesource.com












