Privacy risks in Android smartphones have become a pressing concern in our increasingly digital world. Recent research conducted by UK university scholars has shed light on the privacy issues surrounding popular Android devices. The study revealed alarming data collection practices by customized Android variants, with Google emerging as the primary recipient of this data. Pre-installed third-party apps and encrypted data within system apps further compound the privacy challenges. In this article, we will explore these issues, address user concerns, and provide essential tips to enhance the security of your Android device. Let's dive in.

Privacy Issues in Android Smartphones - A University Study
A comprehensive study conducted by university researchers in the UK delved into the world of Android devices, specifically focusing on major manufacturers like Samsung, Xiaomi, Realme, and Huawei. The study also ventured into the realm of Android forks, examining LineageOS and /e/OS to uncover privacy concerns associated with customized Android variants. The results of this study have raised significant concerns surrounding the transmission and collection of data within these devices.
One of the pivotal findings of the study reveals the extensive transmission of user information by customized Android variants to both the OS developer and third-party entities. This sharing of data extends to system apps pre-installed by vendors as well as prominent third-party platforms including Google, Microsoft, LinkedIn, and Facebook. Of utmost concern is the collection of sensitive user data such as persistent identifiers, app usage details, and telemetry information. Alarmingly, Android users have no control over opting out of this continuous and involuntary data collection process.
Unveiling Google as the primary recipient of collected data across all Android variants is not surprising. However, the presence of third-party apps exacerbates the issue at hand. These apps silently collect user data even when they remain unused and cannot be uninstalled by users. This raises profound privacy concerns as these apps persistently operate in the background, gathering personal information without explicit user consent.
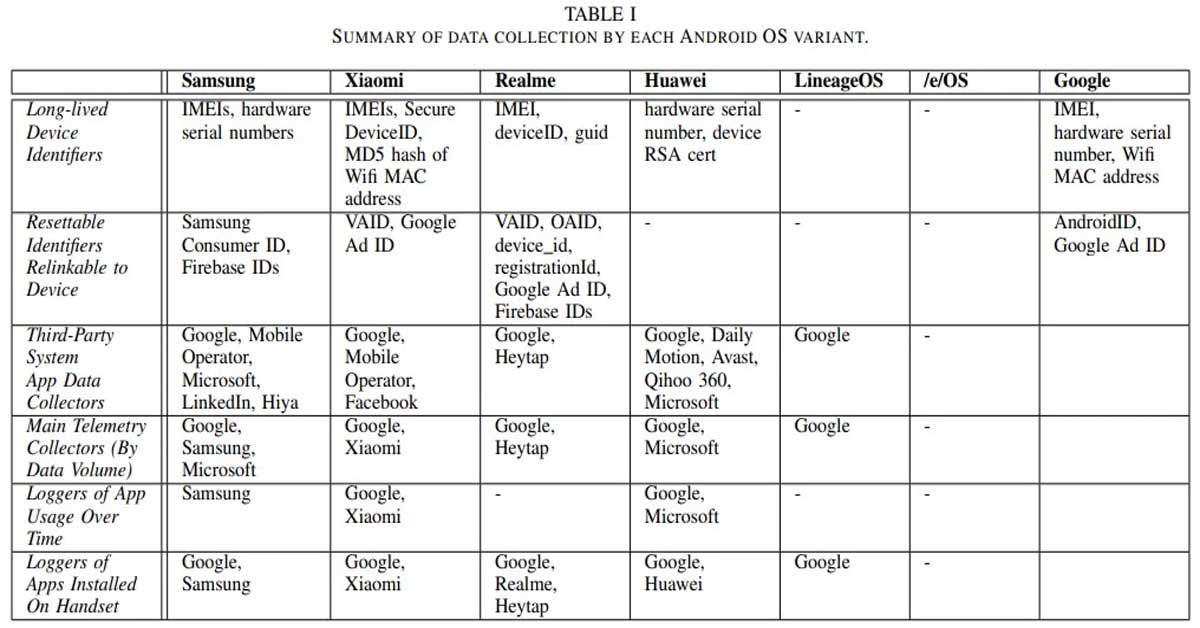
Compounding the problem are vulnerabilities found within certain built-in system apps. Apps like miui.analytics, Heytap, and Hicloud were discovered to have encrypted data that can potentially be decrypted, rendering them susceptible to man-in-the-middle attacks. This underscores the crucial need for robust security measures within the Android ecosystem to safeguard user data from unauthorized access and exploitation.
Adding to the growing unease, the study also investigated various methods employed to deanonymize users. Through the analysis of SIM cards, IMEI numbers, location data history, IP addresses, network SSIDs, or a combination thereof, adversaries can piece together user identities and compromise their privacy.
User Concerns and Requests for Privacy Guidelines
User concerns regarding privacy and their requests for privacy guidelines have become increasingly prevalent in today's digital landscape. Data from Kaspersky's Privacy Checker website sheds light on the preferences and interests of users, providing valuable insights into this growing issue.
According to the data, 85% of users express a high interest in setting up privacy settings specifically for Android services. This highlights individuals' importance in protecting their personal information and maintaining control over their digital privacy. Users are actively seeking ways to safeguard their data within the Android ecosystem.
Furthermore, users are concerned about digital privacy as a whole. In a survey conducted, a remarkable 80% of respondents expressed worry about the topic. This emphasizes the urgent need for robust privacy measures and guidelines to address these concerns and instill a sense of security among users.
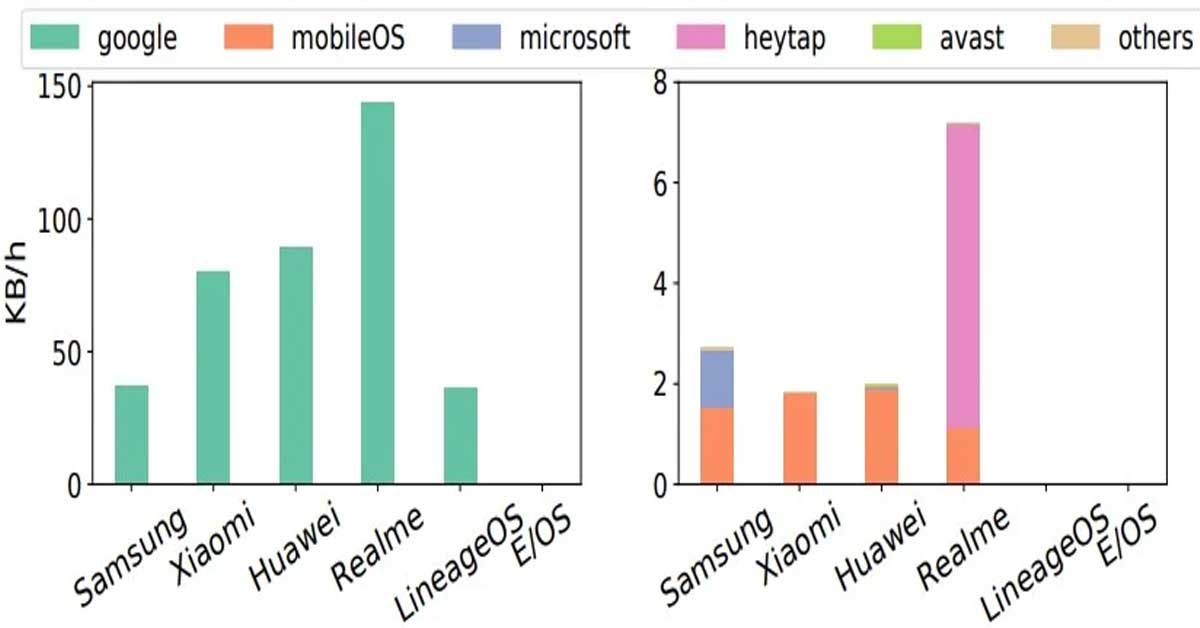
Regarding privacy guidelines, Android services stand out as the most sought-after among users. The number of requests for privacy guidelines for Android services surpasses those for other operating systems. This indicates the pressing demand for clear instructions and best practices to enhance privacy within the Android environment.
When examining the most viewed pages on the Privacy Checker website, it becomes evident that users show a particular interest in Android-related instructions. Among these, medium-level privacy settings for Google attract the highest number of requests, accounting for 17% of the total. Users value a balance between privacy and functionality regarding Google services.
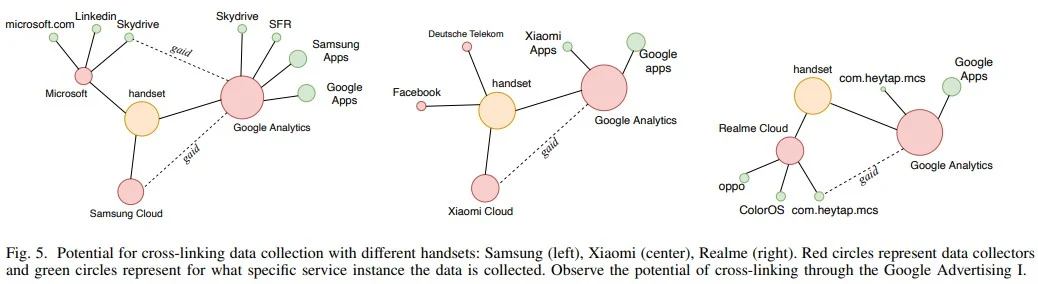
Significant requests are also observed for medium-level privacy rules for other popular platforms such as Chrome and WhatsApp. But, interestingly, users also express a keen interest in the strictest privacy guidelines for Google. This underscores the importance of tailored privacy settings that cater to individual needs and preferences.
Importance of Mobile Security
Our smartphones have become repositories of sensitive information, from personal photos and messages to financial data and login credentials. As a result, we must prioritize security when selecting our devices and the applications we use.

User preparedness plays a crucial role in mobile security. Awareness of potential threats and safe browsing habits can significantly reduce the risk of falling victim to cyberattacks. Equally important is the design of secure platforms and apps. Developers must implement robust security measures to protect user data and prevent unauthorized access.
Regarding mobile security, there are several common threats that users need to be aware of. First, malware attacks pose a significant risk, with Trojans, spyware, and viruses being the most prevalent types. This malicious software can infiltrate our devices, compromising our privacy and potentially causing extensive damage.
Cyber scams are another menace in the mobile security landscape. Phishing attacks are alarmingly common, where attackers masquerade as legitimate entities to trick users into revealing sensitive information. Social media scams, which exploit users' trust and personal information, are also rising.
The threat of malicious data breaches or leaks is ever-present. Cybercriminals target vulnerabilities in systems and apps to gain unauthorized access to sensitive data, which can then be sold or used for malicious purposes. The potential repercussions of such breaches can be devastating for individuals and organizations.
Weak security features and software or hardware vulnerabilities further compound the risks. Outdated software, unpatched vulnerabilities, or even hardware flaws can allow attackers to exploit our devices. Therefore, we must stay vigilant and ensure our devices and apps are regularly updated with the latest security patches.
A Google spokesperson has provided the following comment on the findings of the study:
While we appreciate the work of the researchers, we disagree that this behavior is unexpected – this is how modern smartphones work. As explained in our Google Play Services Help Center article, this data is essential for core device services such as push notifications and software updates across a diverse ecosystem of devices and software builds. For example, Google Play services uses data on certified Android devices to support core device features. Collection of limited basic information, such as a device’s IMEI, is necessary to deliver critical updates reliably across Android devices and apps.
Security Measures and Tips for Android Users
When it comes to protecting the security of an Android device, there are several key points you need to keep in mind. First, Android's open-source nature offers both advantages and challenges. It enables development by an ever-expanding community of developers while potentially opening the door for security vulnerabilities that must be guarded against. Luckily, Google has taken proactive measures that protect both their users' data and themselves and has taken measures such as encryption that effectively safeguard user identities and their devices.
One key step to maintaining mobile security on an Android device is keeping its OS up-to-date with regular system updates that contain security patches for newly discovered vulnerabilities, like those discovered over time. By regularly upgrading, you ensure you receive all of the most up-to-date enhancements and bug fixes. Likewise, exercise caution when downloading applications and stick with trusted sources like Google Play that have stringent security checks in place rather than downloading from unknown sources. This helps lower the risk of malware threats or security risks.
Additionally, to regular updates, additional security tools may help further protect your Android device. For example, antivirus programs like Kaspersky Antivirus for Android provide extra defenses against malware and potential threats, while Samsung Knox offers enhanced data security features designed to safeguard it.
Remember that no single device or operating system offers universal security solutions. Instead, this decision depends on individual needs and preferences, including factors like the level of protection offered, frequency of updates, and features tailored specifically for you. To further increase mobile security, you can follow a few practical tips.
First and foremost, always shop from official app stores, reading user reviews before downloading an application to ensure its safety. Regularly updating the operating system on your device should also be prioritized, and if a manufacturer no longer supports a specific model device consider replacing it to prevent security vulnerabilities from emerging.
Remote data wiping can be an essential step if your device becomes lost or stolen, providing the means for remote deletion of all of its information to protect personal privacy and prevent unwarranted access to sensitive work-related files. When provided by employers, however, data protection policies must also be observed strictly so as not to risk sensitive work-related information falling into unintentional hands.
Implementing strong password protection and multifactor authentication are necessary security measures. Create unique, robust passwords for each of your accounts on all your devices; additionally, turn on multifactor authentication whenever possible for extra layers of protection.
Although convenience should always come first, security must always come before any other factor. When giving permissions for apps or features you need, be wary when giving access. Also, consider technologies like virtual private networks (VPN) that encrypt internet traffic and protect data while connecting to public WiFi networks.

You are more than just a user. You're also an advocate of your privacy. Accept the responsibility and empower yourself. Inspire others to join you in the fight for a digital world that is more secure and respects privacy. Your future is in your own hands.
Sources: nytimes.com / bleepingcomputer.com / heimdalsecurity.com / researchgate.net / techrepublic.com / kaspersky.com / forrester.com /













