Today's digital environment presents cybersecurity threats at every turn. Even highly secure systems may still contain vulnerabilities that need protection. For example, Microsoft recently issued an update to address a security flaw that allowed attackers to circumvent patches for an Outlook zero-day vulnerability exploited in the wild. Ben Barnea of Akamai discovered this issue, which affected all supported versions of Windows.
What made this vulnerability particularly alarming was its exploit by state-sponsored hackers, raising concerns over growing cyber threats faced by governments, businesses, and individuals alike. In this article, we will dive further into details surrounding Outlook's zero-day vulnerability and why applying the latest security updates helps defend against such attacks. We will investigate in detail Outlook's zero-day vulnerability and why applying security updates helps shield from these types of attacks.
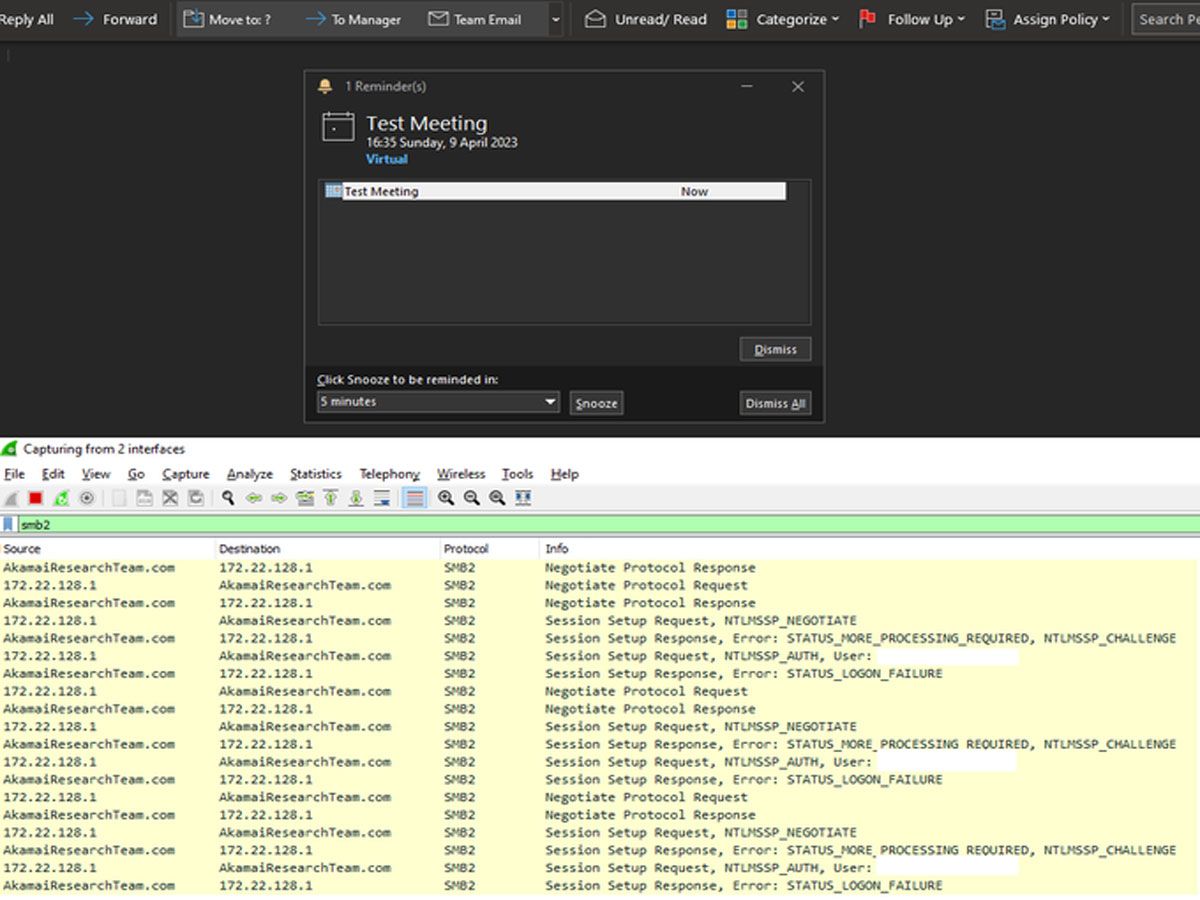
The vulnerability, identified as CVE-2023-29324, affected all supported versions of Windows and was reported by Akamai security researcher Ben Barnea. The Outlook zero-day bug, CVE-2023-23397, was a privilege escalation flaw in the Outlook client for Windows. It allowed attackers to steal NTLM hashes without user interaction in NTLM-relay attacks. Threat actors could exploit the vulnerability by sending messages with extended MAPI properties containing UNC paths to custom notification sounds, causing the Outlook client to connect to SMB shares under their control.
Microsoft addressed the issue by including a MapUrlToZone call to ensure the UNC paths don't link to internet URLs and replacing the sounds with default reminders if they did. However, while analyzing the CVE-2023-23397 mitigation, Barnea discovered a zero-click bypass that allows attackers to circumvent Microsoft's patch.
The bypass tricks the MapUrlToZone checks into accepting remote paths as local paths, causing the Windows Outlook client to connect to the attacker's server. Microsoft warns that customers must install the updates for CVE-2023-23397 and CVE-2023-29324 to be fully protected.
The vulnerable MSHTML platform is still being used by some apps through WebBrowser control and Internet Explorer mode in Microsoft Edge. Therefore, Microsoft urges customers to install this month's security updates and the IE Cumulative updates released to address the CVE-2023-29324 vulnerability to stay fully protected.
Microsoft revealed that Russian APT28 state hackers exploited the vulnerability in attacks against at least 14 government, military, energy, and transportation organizations between mid-April and December 2022. APT28 has been linked to Russia's military intelligence service, the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU).
The threat actors used malicious Outlook notes and tasks to steal NTLM hashes by forcing their targets' devices to authenticate to attacker-controlled SMB shares. These stolen credentials were also used for lateral movement within the victims' networks and to change Outlook mailbox permissions to exfiltrate emails for specific accounts.
Microsoft released a script to help Exchange admins check if their servers were breached but also advised them to look for other signs of exploitation if the threat actors cleaned up their traces.
In addition to fixing the Outlook zero-day flaw, Microsoft pushed a security update for Windows 11 on May 9, 2023, which included fixes for 38 flaws, including three zero-day vulnerabilities. Additionally, six vulnerabilities patched in the update were deemed 'Critical' as they allowed remote code execution.
A patch for the BlackLotus bootkit vulnerability was deployed but needed to be manually enabled. Additionally, a security update released on May 5 for Microsoft Edge fixed 11 vulnerabilities.
Remember that 0-click Outlook vulnerability with a custom sound leading to NTLM theft?
— Akamai Security Intelligence Group (@akamai_research) May 10, 2023
Akamai researchers found a way to bypass the patch to it.
In our write-up, see how adding a slash allowed for a bypass.https://t.co/eO121SaZur pic.twitter.com/YrrBikMZqj
Akamai researcher Ben Barnea found a new important vulnerability in an Internet Explorer component, assigned CVE-2023-29324 with a CVSS base score of 6.5. The vulnerability causes a Windows API function MapUrlToZone, to think that a remote path is a local one incorrectly.
MapUrlToZone is commonly used as a security measure. In particular, it was used to mitigate the critical Outlook vulnerability CVE-2023-23397 patched in the March Patch Tuesday.
An unauthenticated attacker on the internet could use the vulnerability to coerce an Outlook client to connect to an attacker-controlled server, resulting in NTLM credentials theft. It is also a zero-click vulnerability, meaning it can be triggered with no user interaction.
Microsoft's recent discovery and resolution of security vulnerabilities underscore the significance of remaining vigilant regarding software updates and patches.
Recognizing and acknowledging the efforts of security researchers and organizations like Microsoft in discovering and fixing these vulnerabilities is also significant. Without their tireless work, cybercriminals would wreak even more destruction on our digital lives, as recent discoveries demonstrate there will always be new vulnerabilities to find and address.
As individuals and organizations alike, we should remain proactive and vigilant regarding cybersecurity by staying informed and taking effective security steps to secure ourselves and our data from cyber attacks. Let us all pledge our dedication to making the digital world safer together!
Sources: microsoft.com / akamai.com / bleepingcomputer.com












