An insidious exploit that allowed attackers to inject the notorious NSO Group's Pegasus spyware into iPhones went unnoticed for a while. But thanks to the vigilant efforts of security experts and swift action from Apple, your devices can breathe easy again.
Pegasus, the nefarious spyware developed for governments and law enforcement, is at the heart of this story. Pegasus peddled to countries often accused of human rights violations. Basically, it's a weapon used to target individuals like journalists and political opponents, putting their lives and data in jeopardy.
What is Pegasus, and who or what is NSO Group?
Pegasus, an intricate spyware program crafted by the Israeli company NSO Group, quietly operates as a favored tool within government circles.
This advanced software silently breaches the targeted individual's smartphone, clandestinely retrieving a trove of data encompassing photographs, text messages, and audiovisual recordings.
What truly sets Pegasus apart is its claim of being untraceable back to the employing government, making it an invaluable asset for covert operations. NSO Group officially asserts that their software aids government intelligence and law enforcement agencies in grappling with encryption challenges during counterterrorism and criminal inquiries.
Nonetheless, this for-hire spyware endeavor has stirred notable apprehension among civil liberties advocates. While NSO Group maintains its exclusive association with government bodies and vows to terminate access upon abuse detection, skepticism lingers.
Amnesty International, in particular, expresses deep concern over potential supply of spyware to oppressive regimes, where governmental intentions may not align with the welfare of their citizens.
Apple's battle against the NSO Group escalated when they sued them in November 2021, setting the stage for a high-stakes showdown.
The exploit that paved the way for Pegasus' infiltration was anything but ordinary. It operated stealthily on iOS, and victims were oblivious to its presence. Here's how it unfolded:
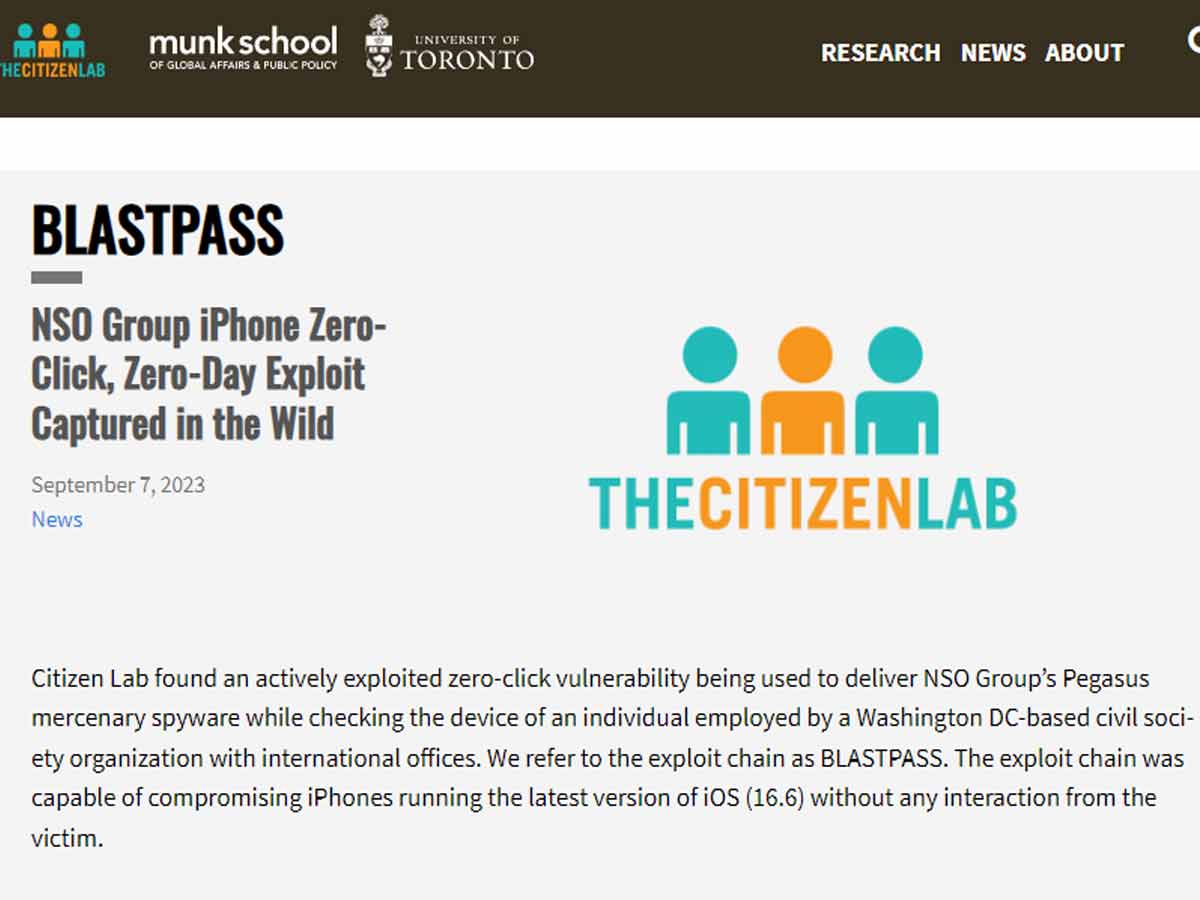
Citizen Lab's Discovery
Citizen Lab, a prominent group dedicated to investigating government malware, played a pivotal role. They stumbled upon a zero-click exploit on iOS, a vulnerability that allowed attackers to target iPhones running iOS 16.6 without any interaction from the victim.
Named BLASTPASS, this exploit chain compromised iPhones without any victim interaction. Attackers used PassKit attachments containing malicious images sent via iMessage to deliver their payload. The implications were profound - even the latest iOS version (16.6) was susceptible.
Apple's Rapid Response
As soon as Citizen Lab uncovered this vulnerability, they promptly reported it to Apple. The tech giant didn't waste a moment and swiftly released a patch - iOS 16.6.1. Notably, they acknowledged Citizen Lab for their contribution. This immediate response showcased Apple's commitment to safeguarding its users.
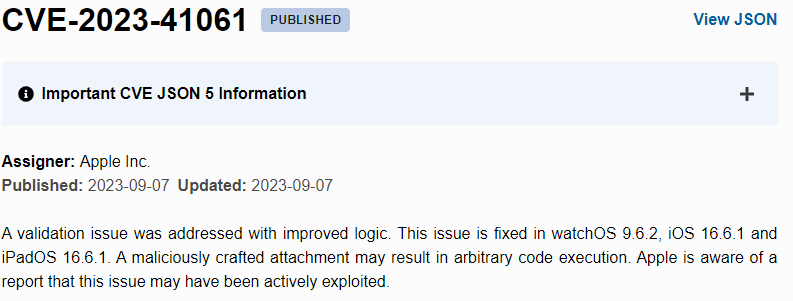
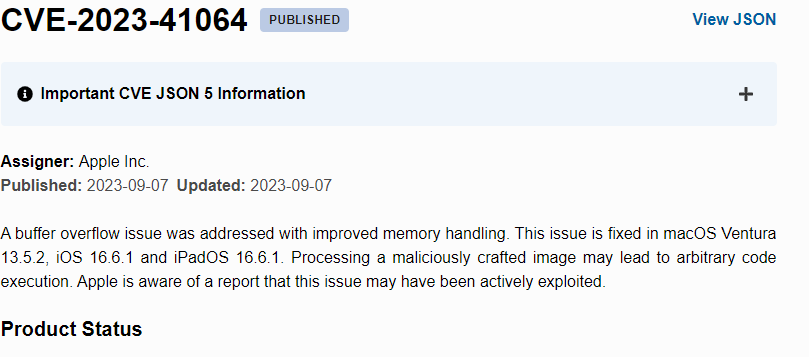
To track and communicate vulnerabilities like this, Citizen Lab relied on Common Vulnerabilities and Exposures (CVEs). In this case, two were issued - CVE-2023-41064 and CVE-2023-41061, adding transparency and accountability to the situation.
The first step is to update your device. iOS 16.6.1 is readily available, and you can access it through your device's settings. Navigate to Settings > General > Software Update and ensure you have the latest security patches.
For those facing increased risks due to their roles or activities, enabling Lockdown Mode is crucial. It acts as an added layer of defense against sophisticated attacks like the one involving Pegasus.
This entire incident underscores the relentless targeting of civil society by highly sophisticated exploits and mercenary spyware.












