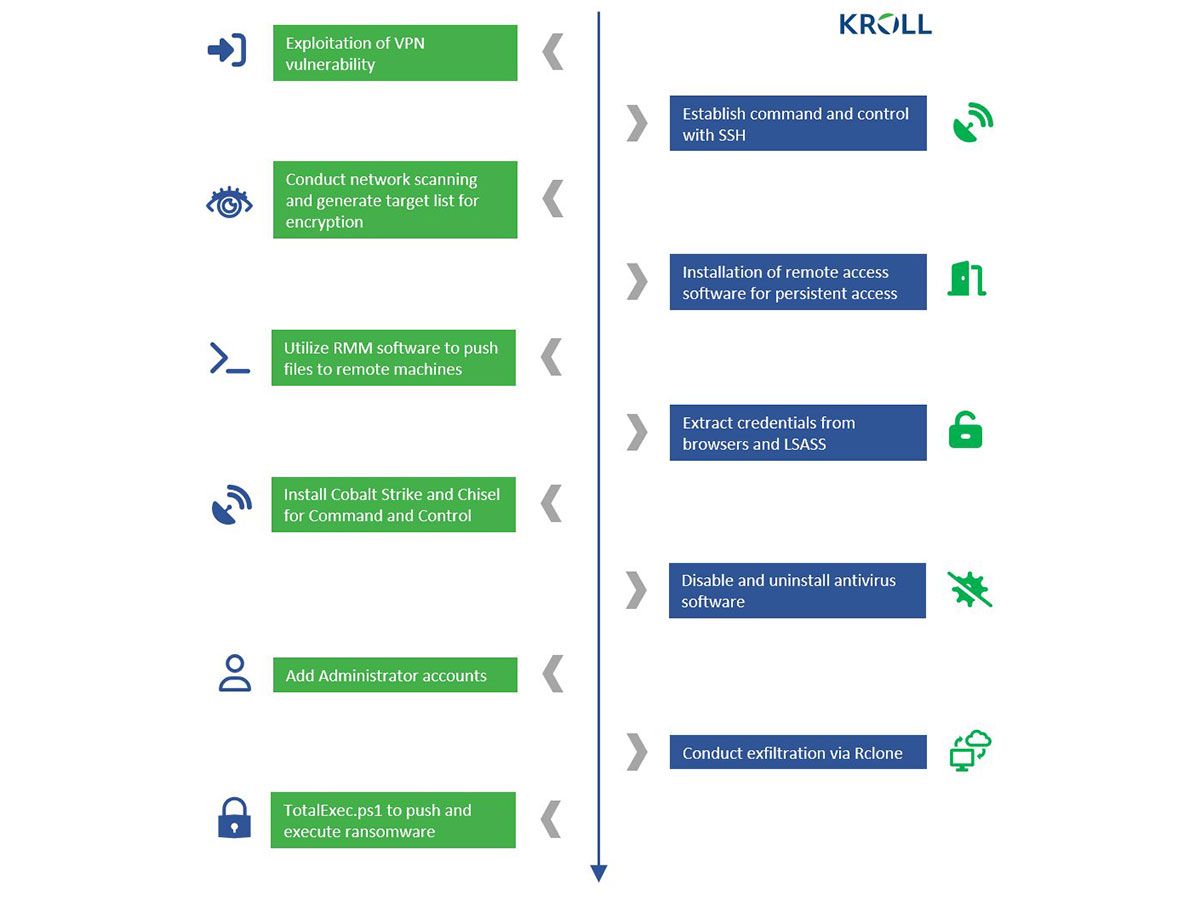
Ransomware attacks are nothing new in the world of cybersecurity. However, the latest addition to this list is a group known as Cactus. This newly discovered threat actor has been actively targeting large commercial entities since March. Their unique approach to avoiding detection sets them apart from other ransomware groups. Cactus has found a way to exploit known vulnerabilities in Fortinet VPN appliances and pivot inside from a VPN server with a VPN service account. Once inside, they use encryption to protect their ransomware binary, making it difficult to detect.
Their tactics include stealing data from their victims and transferring it straight to cloud storage using the Rclone tool. If that's not enough, they have also added a new twist to their game – threatening to publish their victim's stolen files unless they comply with their demands. This new ransomware group has made its way into the cybersecurity world, and its methods are raising alarms across the industry. In this article, we'll dive deep into the tactics used by Cactus and how it has been able to evade detection.
Cactus' Unique Tactics
Cactus has a unique way of encrypting itself, making it difficult to detect, and it can evade antivirus and network monitoring tools. In addition, the ransomware changes the extensions of its target files depending on their processing state. This tactic makes it difficult for defenders to track which files have been affected and which have not.
Cactus relies on SoftPerfect Network Scanner (netscan) to look for interesting targets on the network, and it uses PowerShell commands to enumerate endpoints and identify user accounts. This allows the ransomware to spread laterally within the victim's network and maximize the endpoints affected.
Cactus ransomware also steals data from victims and transfers files straight to cloud storage using the Rclone tool. This tactic allows the attackers to remove the stolen data quickly and efficiently, minimizing the chances of being detected.
The ransomware gang also uses a modified variant of the open-source PSnmap Tool to launch various tools required for the attack. This tool allows attackers to scan for vulnerable systems, launch brute-force attacks, and gather information about the victim's network.
To ensure the attack's success, Cactus operators run a batch script that uninstalls the most commonly used antivirus products. This tactic ensures that the ransomware can operate undetected, and the attackers can carry out their attack without interference.
Modes of Execution
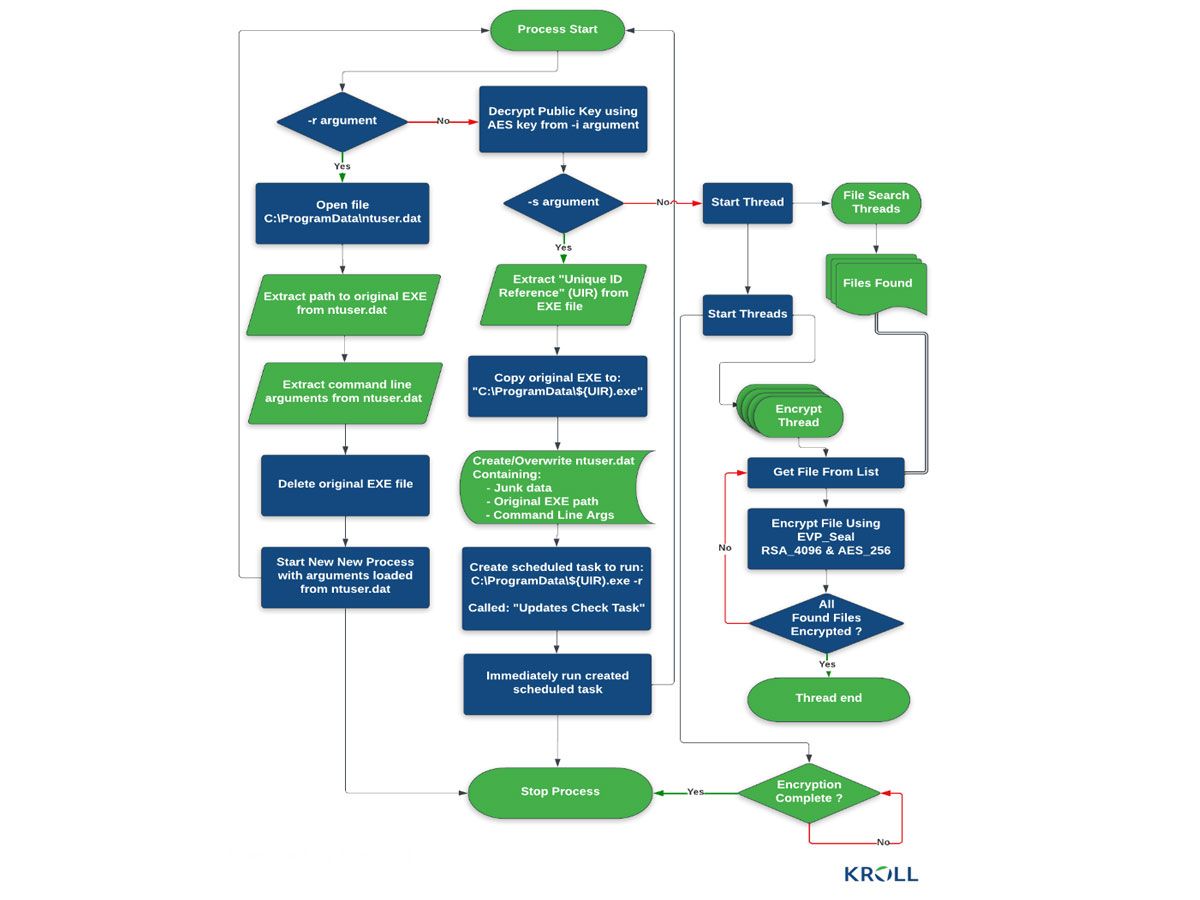
There are three main modes of execution for the Cactus ransomware: setup (-s), read configuration (-r), and encryption (-i). These modes allow the ransomware to prepare the victim's network, gather information about the target, and encrypt the victim's files.
Cactus uses encryption to protect the ransomware binary and deploys it with a specific flag that allows it to execute. The ransomware changes the extensions of its target files depending on their processing state.
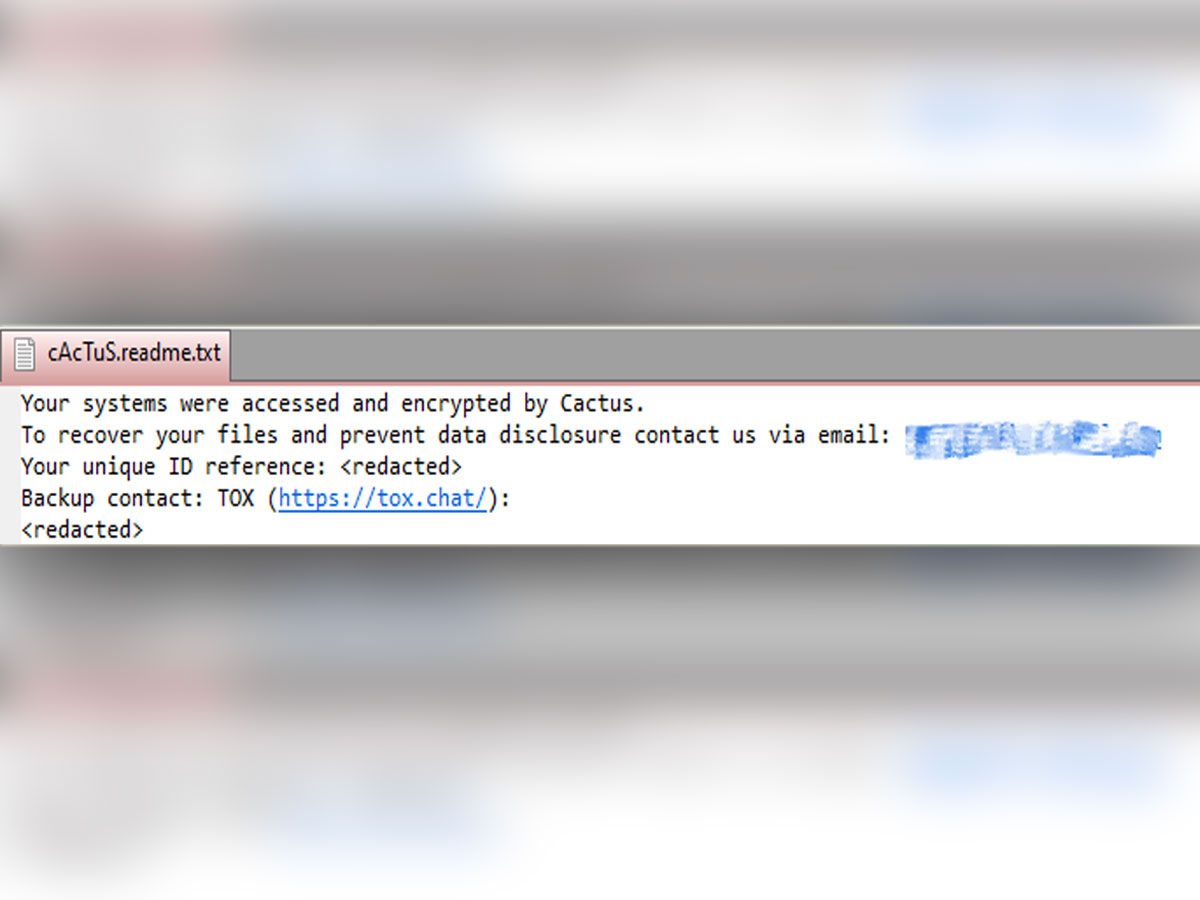
Currently, there is no public information about the ransoms that Cactus demands from its victims, but they are believed to be in the millions. In addition, Cactus threatens victims with publishing their stolen files unless they comply. This tactic puts additional pressure on the victim to pay the ransom, as they face the possibility of reputational damage and legal consequences.
The Cactus ransomware group is just one example of the growing number of cyber threats businesses face. However, organizations can avoid falling victim to these threats and protect their valuable assets by taking the necessary steps to protect themselves.
Source: bleepingcomputer.com / github.com / bitdefender.com / kroll.com












