Amid the ever-changing realm of cybersecurity, the advent of sophisticated smartphone malware presents substantial dangers to the security of user data. For example, Cisco's Talos security team experts have made a breakthrough discovery, revealing the existence of an advanced spyware named "Predator."
This insidious malware can covertly record voice calls and harvest information from widely used applications such as Signal and WhatsApp. Concurrently, India's esteemed national cybersecurity organization, CERT-IN, has issued a cautionary alert concerning a perilous Android malware known as "Daam," which poses a grave threat to user data security.

The Predator Spyware - A Stealthy Threat

In cybersecurity, the Predator Spyware has emerged as a formidable adversary, operating covertly to compromise user privacy and security. Developed by Cytrox, this powerful spyware has found its way into the hands of governments across the globe, highlighting the magnitude of its capabilities. It is worth noting that Predator is part of the Intellexa alliance, a collective that includes other prominent players in the surveillance industry, such as Nexa Technologies, WiSpear/Passitora Ltd., and Senpai.
Government-backed actors have employed Predator in various campaigns, utilizing its sophisticated features to their advantage. The malware is particularly notable for bundling five zero-day exploits, a term used to describe vulnerabilities that are unknown to software vendors and, therefore, lack available patches. Google's Threat Analysis Group has been diligent in tracking the deployment of Predator, identifying its involvement in at least three campaigns. These findings shed light on the alarming scope of the malware's influence.
The targets of Predator's surveillance activities are not limited to ordinary individuals. Ayman Nour, a prominent member of the Egyptian political opposition, and undisclosed journalists living in exile have fallen victim to this invasive spyware. Such high-profile targets further emphasize the potential ramifications of the malware's reach.

Recently, researchers at Talos were able to obtain crucial components of the Predator malware designed specifically for Android devices. This breakthrough has allowed for a deeper understanding of the malware's inner workings and the extent of its capabilities. At the core of Predator's operation are two main components: Predator itself and Alien. While initially considered a mere loader for Predator, Alien is now known to actively implement low-level capabilities essential for surveillance activities.
To gain control over targeted devices, Alien exploits vulnerabilities such as CVE-2021-37973 and CVE-2021-1048. These vulnerabilities provide a gateway for the malware to establish a foothold on the device, enabling it to carry out its insidious operations undetected. This revelation underscores the level of sophistication embedded within the Predator malware and the deliberate efforts made to evade conventional security measures.
Alien and Predator - A Lethal Duo
The combination of Alien and Predator proves to be a lethal force when it comes to infiltrating Android devices and evading security features. One of the key hurdles for malware like Predator is SELinux, a security feature that guards the communication channels between different processes on an Android device. However, Alien and Predator have devised a way to work together and bypass SELinux, allowing them to carry out their malicious activities undetected.

Alien, the companion component to Predator, plays a critical role in this intricate dance of evasion. By exploiting vulnerabilities within the Android system, Alien gains control over targeted devices. These vulnerabilities, such as the likes of CVE-2021-37973 and CVE-2021-1048, serve as gateways for Alien to establish its foothold and pave the way for the subsequent actions of the malware.
Data collection lies at the heart of Predator's objectives, and Alien's functionality facilitates this stealthy operation. One ingenious method employed by Alien is the storage of recorded audio in a shared memory area. By doing so, the malware successfully bypasses the restrictions imposed by SELinux, which would typically prevent such unauthorized access. This maneuver allows Predator to discreetly store the pilfered audio before exfiltrating it for further exploitation.
Predator consists of two primary components that enable its spyware capabilities: Tcore and Kmem. Tcore serves as the main component and encompasses a range of functionalities crucial to the spyware's operations. This includes the ability to record audio and collect data from popular apps, such as Signal and WhatsApp. Additionally, Tcore allows for the concealment of applications and the prevention of their execution upon device reboot.
On the other hand, Kmem plays a pivotal role by providing Predator with kernel access. This access, made possible through Alien's exploitation of vulnerabilities like CVE-2021-1048, enables the spyware to execute its functions seamlessly. By having such deep-rooted access to the kernel, Predator can operate with greater control and efficiency, maximizing its impact on the compromised device.
The Daam Malware
The Daam malware has caught the attention of India's national cybersecurity organization, CERT-IN. Their recent warning sheds light on the significant threat that Daam poses to user data security. This sophisticated malware has the capability to bypass antivirus software, stealthily steal sensitive information, and even install ransomware on targeted devices, leaving users vulnerable to devastating consequences.
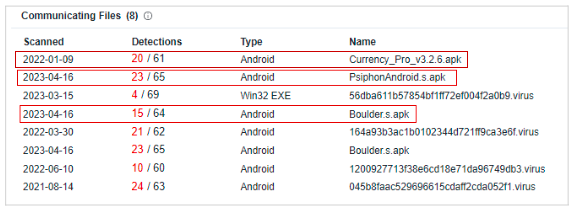
Once Daam infiltrates a device, it proceeds to access a wide array of confidential data. From browsing history and call logs to contact information, camera contents, SMS messages, and files, the malware leaves no stone unturned in its quest for valuable information. Users unknowingly become victims of this invasive malware, unaware of the extent to which their personal data is compromised.
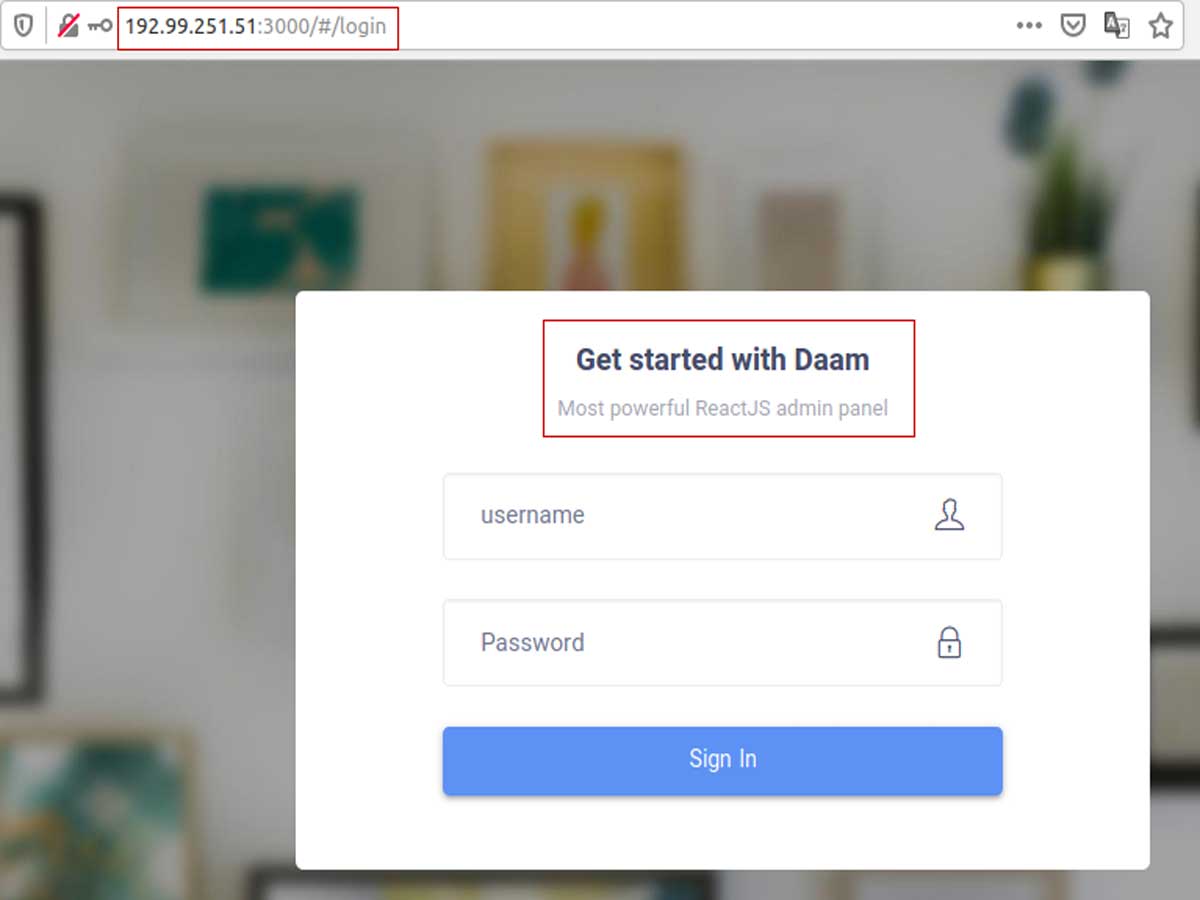
One particularly troubling aspect of Daam is its employment of encryption techniques and ransom notes. Utilizing AES encryption, the malware encrypts the device's contents, rendering them inaccessible to the rightful owner. This encryption process generates ".enc" files and leaves behind a chilling ransom note demanding payment for the release of the encrypted data. The implications of such actions are grave, leaving users in a desperate situation, grappling with the loss of their personal information and the threat of financial extortion.
To safeguard against the pernicious Daam malware and similar risks, CERT-IN recommends several best practices. Firstly, users are advised to limit their downloads to official app stores, as these platforms tend to have stricter security measures in place. Additionally, reviewing app details and verifying app permissions can provide valuable insights into the legitimacy and privacy practices of the apps in question. It is also crucial to avoid side-loading apps from untrusted sources, as they often serve as gateways for malware infiltration.
Keeping devices updated with the latest patches is of utmost importance, as software updates frequently address security vulnerabilities. By regularly installing updates, users can significantly reduce their exposure to threats like Daam. Practicing caution when browsing the internet is also essential. Staying away from untrusted websites and suspicious links helps mitigate the risk of inadvertently downloading malware.
To fortify defenses further, utilizing antivirus software is highly recommended. These tools provide an additional layer of protection against known malware variants, including Daam. Verifying the sender information of SMS messages and conducting thorough research before clicking on links can prevent falling victim to phishing attempts and other forms of social engineering.

It is also essential to remain vigilant when it comes to verifying URLs and utilizing safe browsing tools. By confirming the authenticity of websites and employing safe browsing practices, users can minimize their exposure to potential threats. Lastly, promptly reporting any suspicious activity to the relevant authorities helps in identifying and addressing emerging malware campaigns, ultimately contributing to the collective effort to combat the Daam malware and safeguard user data.
In today's digital landscape, the proliferation of smartphone malware has become a serious concern for user data security. With malware like Predator and Daam becoming increasingly sophisticated, it is imperative for users to remain alert and take necessary precautions to protect their personal information and maintain online security. By delving into the intricacies of these malware and adhering to the guidelines put forth by CERT-IN, individuals can effectively counteract the risks imposed by these malicious threats and safeguard their digital lives.
Sources: gizmochina.com / talosintelligence.com /arstechnica.com / cert-in













