In today's digital world, passwords are the keys to our virtual kingdoms. They're the first line of defense against hackers, malicious actors, and other cyber threats. But have you ever stopped to consider how passwords came to be and how they've evolved? From the humble beginnings of simple letter combinations to the complex algorithms of modern-day cryptography, passwords have a rich history worth exploring. In this article, we'll delve into the fascinating evolution of passwords from their earliest days to today's cutting-edge technology. So buckle up and get ready to explore the secrets behind the humble password.
Historical Uses of Passwords

Passwords have long been employed to protect sensitive information, control access to restricted areas, and secure valuable assets. Their origin can be seen in ancient civilizations when watchwords were used to identify friendly troops against enemy infiltration. Later, military passwords became widely adopted by governments and intelligence agencies to secure classified information and maintain operational secrecy.
Popular culture depicts passwords as magical codes that grant access to hidden treasure or forbidden areas, frequently depicted in movies and books as mystery and intrigue-building devices. But in today's computer-centric society, passwords have become indispensable to security measures protecting personal data, financial transactions, and digital assets from unwanted intrusions.

However, passwords have also created security challenges and issues. For example, weak passwords can easily be cracked or guessed, as stolen ones could lead to identity theft and financial fraud if stolen and used without authorization. In response to these vulnerabilities, efforts have been made to develop alternative authentication methods like biometrics and two-factor authentication to improve online security and reduce our reliance on passwords.
The Rise of Computer Passwords
Since computers became part of daily life, passwords have become essential to online activities. From email access and bank account logins, passwords have become indispensable tools in securely protecting our online activities. The first password system ever developed was in the early days of computing to protect mainframe computers by requiring users to enter both a username and password for entry. Unfortunately, these early systems only permitted four-character passwords, which made access easy to guess or breach.

As computing technology advanced, so did the need for stronger password security. Encryption algorithms enabled longer and more complex passwords that were harder for hackers or guessers to guess or crack; additionally, multi-factor authentication, such as fingerprint verification or one-time codes, has added another safeguard against hacks or guessers.
Though technological progress continues apace, password security remains an ongoing problem. People tend to choose passwords that are easy to remember, like their pet's name or birthdate, making them easy for hackers to guess and reuse across multiple accounts, giving access to multiple hacker attacks with one stolen password. As a result, companies have implemented tighter policies requiring their employees to change passwords regularly to minimize potential security breaches.
Password Security Today

Recently, security advice regarding passwords has changed considerably. Where it used to be recommended that passwords should be regularly changed, including uppercase, lowercase letters, numbers, and symbols, experts now advocate using longer and more complex phrases instead.
This new approach to password creation relies on the idea that longer passwords are harder for humans to guess or crack than shorter ones, even without special characters or numbers being included. So, for example, a random phrase such as "purplebananafrogjumping" would be harder for someone else to guess or crack than something as short and sweet as "P@ssw0rd."
Experts strongly advise creating unique passwords for each account to prevent hackers from breaking in multiple times with one stolen password. Although managing passwords manually may seem cumbersome and challenging, using a password manager makes creating and saving unique ones simpler than ever. Long phrases make passwords easier to remember and reduce the chance that they need to be written down or stored using insecure methods such as document storage on computers or phones.
Password Protection Techniques
As well as using strong passwords, other measures can also help protect them. For instance, various techniques exist which can protect passwords against being breached.

Hashing involves turning passwords into unique strings of characters for storage in databases. When users enter their password, their system compares it with what has already been stored. Even if an attacker gains access, their view would only consist of this hashed version, which renders their original password useless.
Salting involves adding an unpredictable string of characters before hashing a password, adding another level of defense against attack. So even if an attacker gains entry to your database and sees hashed passwords, they can only crack them after first knowing their salt value.
Multifactor authentication has quickly become one of the go-to strategies for password security, requiring multiple forms of identification to gain entry to accounts, for instance, fingerprint scans or SMS codes sent directly to their phone as additional forms of proof that even if someone stole their password, they can't gain entry due to additional factors of authentication. This way, even if attackers gain entry via a stolen password, they will only gain entry if they provide more proof.
What is a Passphrase? And Why Are Passphrases Considered Superior to Passwords?
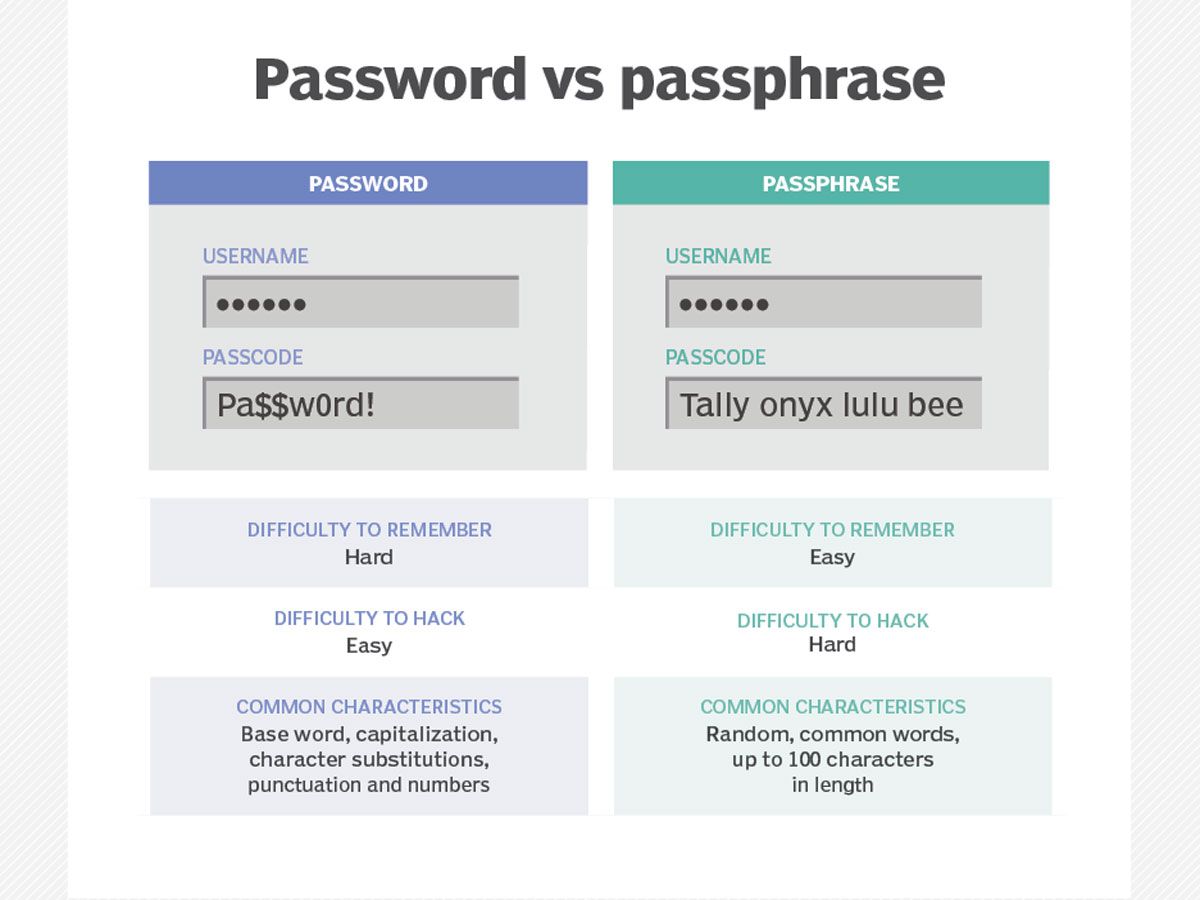
In addition to traditional passwords, another method of user authentication they can employ to safeguard accounts and devices is using passphrases. Passphrases differ from traditional passwords by being longer strings of words that reach over 100 characters long, making them memorable and difficult for attackers. Their advantage over regular passwords lies in adding random elements, which lessen predictability to keep accounts safe from attack.
Passphrases may be an effective alternative to passwords in places that accept longer characters, including Windows and macOS operating systems and encryption keys. Password manager applications or services also often rely on passphrases as a secure means of remembering common passwords that can be hard to recall. Their ease of memory makes them an attractive solution that offers both convenience and protection.
Passphrases offer more secure solutions than passwords and can often be harder for even advanced password-cracking tools to crack. To create a strong passphrase, it is recommended that an easy-to-remember but uncommon group of four to eight words with spaces between and within words is selected, capital letters used when necessary (excluding certain words ), the punctuation used, and special characters added that make sense only to you and no one else, unusual spelling variations made of letters together and making some into numbers must all be employed when crafting one.
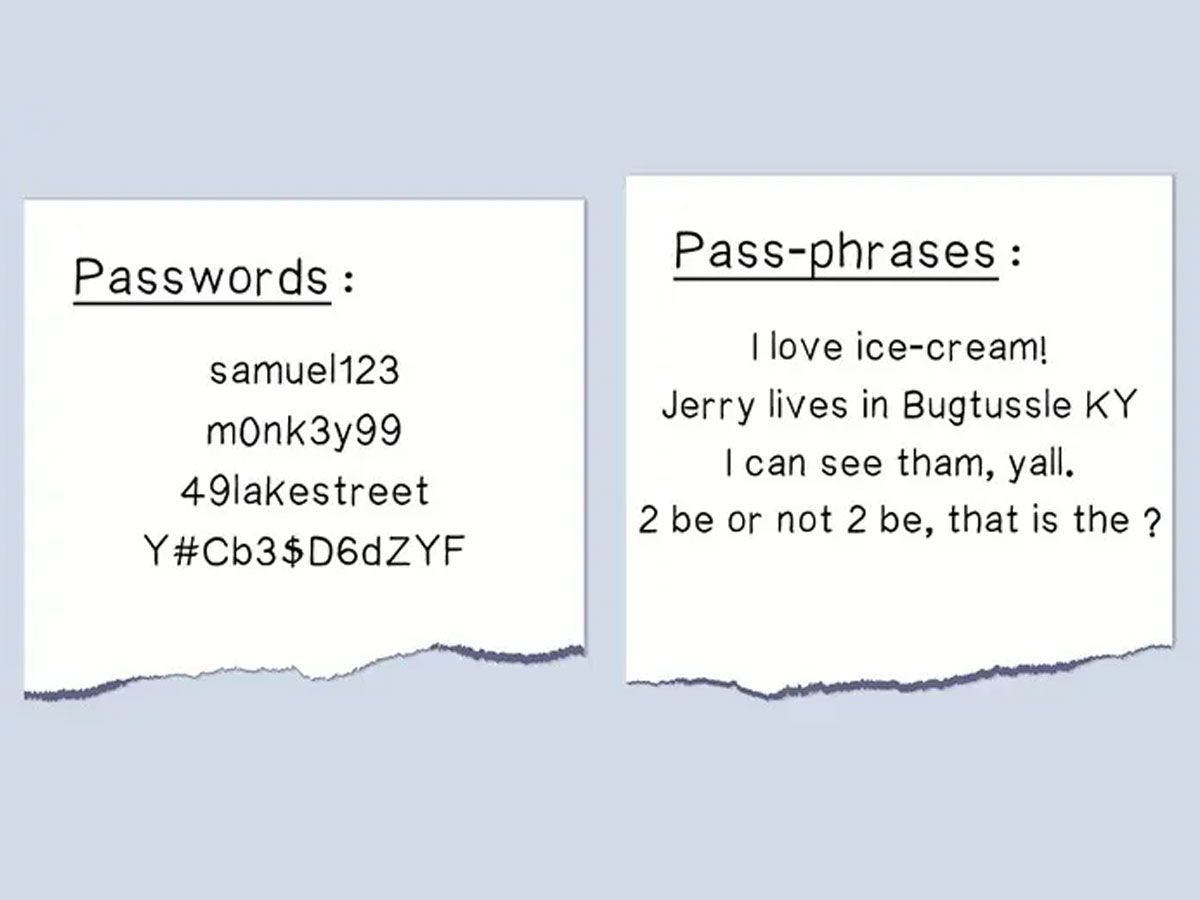
Passphrases are similar to passwords in that they should only be understandable to their intended use to ensure a straightforward and secure creation process. Users can create passphrases using personal stories, memories, keywords, mnemonic devices, or random dice-generated passwords with predetermined word lists or documents. Passphrases offer an effective way to safeguard digital assets against attackers attempting to gain entry, as most modern operating systems, applications, and services accept passwords of up to 100 characters.
This allows users to hide their digital assets behind passwords of over 100 characters, offering secure yet viable protection against attackers. Passphrases provide users a more secure option than traditional 100-character passwords when protecting digital assets against attacks. With more and more applications accepting over 100-character passwords, passphrases are becoming a secure and viable option for protecting digital assets.
Common Password Problems

Although security measures exist to combat password breaches, breaches still happen frequently. One key problem lies with people choosing easy-to-guess passwords, which makes hacker attacks simpler, further compounded by multiple people using one password across several accounts, which increases risk.
Despite being widely known for their security risks, common passwords such as "123456" and "password" continue to remain popular despite widespread knowledge about them. Not only can hackers easily guess these passwords, but hackers also use them as bait when trying to breach an account, leaving these types of protection with very limited protection against unintended access.

Two-factor authentication has become an increasingly popular strategy to tighten password security. This method requires users to provide additional forms of identification like fingerprint scans or one-time codes delivered directly to mobile phone phones and their passwords for added protection. However, while two-factor authentication provides another layer of defense, hackers can only breach accounts with enough persistence and determination.
Companies have taken measures to combat password problems by adopting stricter password policies and informing their users on the importance of strong, unique passwords for each account, encouraging users to utilize password managers that generate these strong, unique passwords, further decreasing the risk associated with reused passwords. By adopting such steps, individuals and organizations can significantly strengthen password security while decreasing risks related to security breaches.
Password Cracking

Password cracking refers to using software programs to discover an unknown or forgotten password for computer or network resources, whether forgotten by itself or by someone else. Although password-cracking programs can serve a good cause, such as recovering passwords for websites or resources that have lost them, password-cracking programs often involve criminal activities, such as uncovering sensitive banking credentials that threat actors use for identity theft or fraud schemes.
Password cracking programs use various strategies to identify passwords. Some rely on lists of frequently used words, while others employ algorithms for more intelligent guesses. Short passwords or predictable patterns such as 1234 are easier to crack.
Strong passwords that are unpredictable and hard to guess must be utilized to prevent password cracking. Passwords that contain personal identifiers or common phrases should be avoided as these could easily be cracked open by cyber criminals. A hash function encrypts strong passwords securely, preventing computers from storing plaintext versions.
Password crackers usually follow four steps when breaking a password:
steal its hash
select an effective cracking technique,
prepare all relevant password hashes
run the cracking tool to reveal it

Cracking techniques include brute force, phishing, and guessing. Cain and Abel, OCRACK, and John the Ripper are the three most frequently used password-cracking tools. While using any such methods or tools to gain access to one's password is legal, using any of them on others (even guessing at their password) without their express consent can result in criminal charges being laid against them.
Password Managers
Recent years have witnessed a surge in password manager usage as an effective method to organize and protect passwords. A password manager is a software application that stores all of a user's online account passwords under one master password instead of having to remember multiple separate ones for different accounts users only need to remember one unique code when accessing their password manager.

One key advantage of password managers is creating strong, complex passwords for each account that are difficult for hackers to crack. Furthermore, password managers can autofill login credentials on users' behalf, saving time and reducing typos when typing passwords manually.
Various password managers are available, both paid and free, with popular examples including LastPass, 1Password, and Dashlane being some of the more well-known examples. Each password manager offers different features and strengths, so it is important to conduct thorough research when choosing one.
Though password managers provide an efficient and secure way to handle passwords, they have some potential drawbacks. For instance, if a master password for the password manager becomes compromised, it could potentially risk all users' passwords. In addition, if the company experiences any security breaches, its users could also become exposed. However, most password managers utilize strong encryption measures and safeguards against data breaches to keep user passwords secure.
Password security cannot be overemphasized, with a strong, unpredictable password essential to protecting digital security in any digital landscape. Individuals should create unique and complex passwords for all online accounts that contain sensitive data like banking accounts or personal data, particularly those containing sensitive financial data or banking account login credentials.
However, password security is only one component of cybercrime defense technology. Cybercriminal tactics continue to evolve at an alarming rate; therefore, individuals must stay abreast of emerging cybersecurity threats and best practices to remain alert and knowledgeable of how best to combat them.
Individuals can protect themselves and their data by aggressively attacking cybersecurity and password security, including regularly updating devices and software, avoiding suspicious links and downloads, and employing safeguards like biometrics and two-factor authentication.
Sources: wsj.com / cisco.com / techradar.com / nordpass.com /dashlane.com / mail.com / securitybrief.co.nz /nvlpubs.nist.gov / cryptosmith.com / techtarget.com













